Flipping the Switch: Business Logic Bypass in [Redacted Legal Search Platform]
Published: April 2025
🧠 TL;DR
In [Redacted Legal Platform], I discovered a simple yet powerful logic flaw that allowed full access to Pro-level search features — without a subscription, login, or authorization. All it took was changing a single query parameter:
searchMode=PROMODE
The app trusted the frontend UI to restrict Pro features, but the backend never validated the user’s subscription or role.
🔢 Why This Was Serious
The Pro plan was a paid tier with features like:
- Advanced municipal law search
- Jurisdiction-wide coverage
- Saved searches and analytics tools
By flipping a single parameter, all these became freely available — representing both financial loss and exposure of premium content.
🔍 Exploit Breakdown
✅ Step 1: Basic User Login
Logged in as a regular (free) user. The UI clearly disabled Pro search features and greyed-out premium tabs.
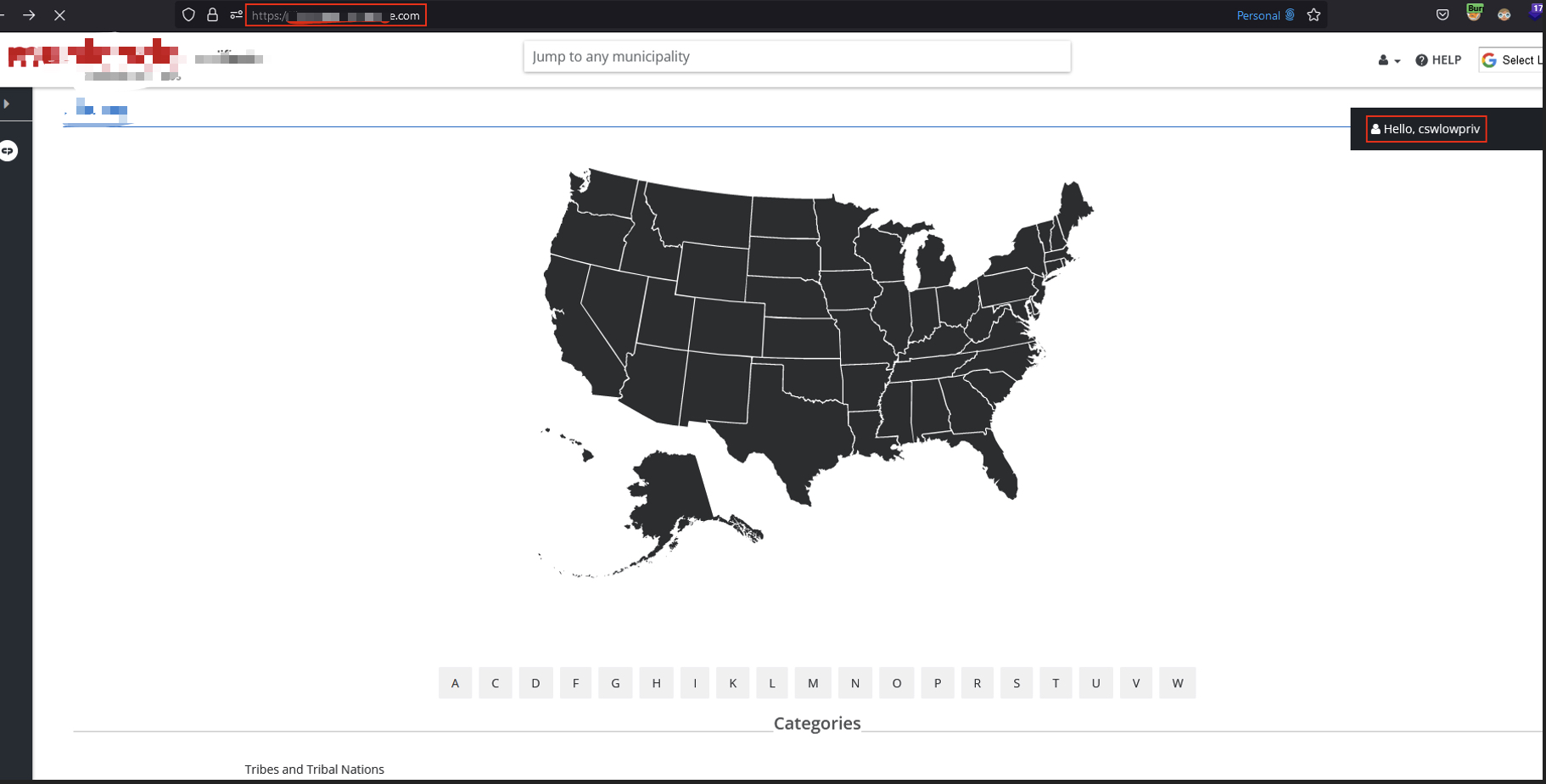
Logged in as a free-tier user. “Pro” features visibly disabled.
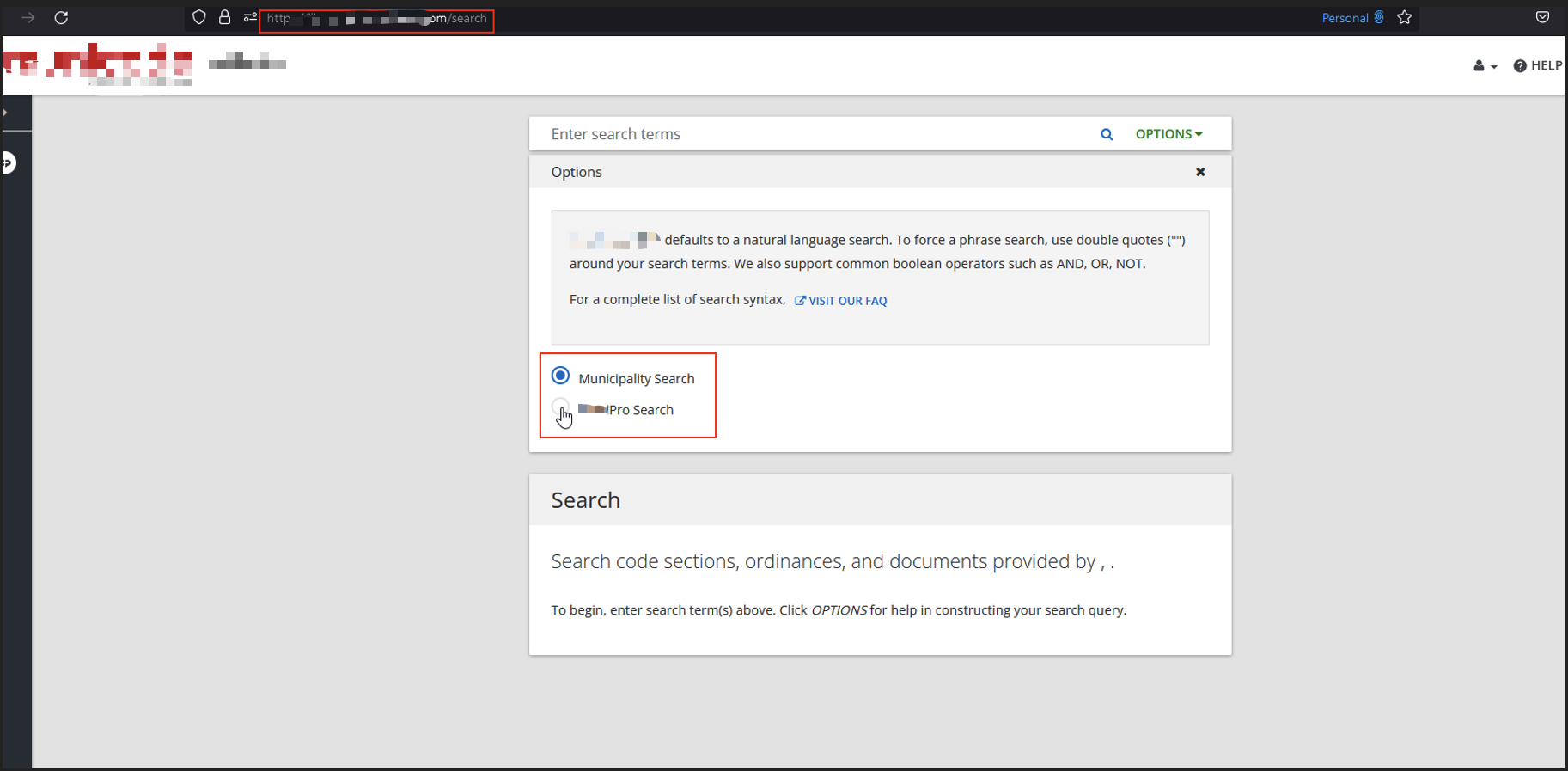
The Pro Search option was grayed out for non-paying users.
✅ Step 2: Modify the Query
Observed normal search requests such as:
https://library.[redacted].com/search?searchMode=MUNICIPAL&searchText=zoning
Changed searchMode=MUNICIPAL to searchMode=PROMODE:
https://library.[redacted].com/search?searchMode=PROMODE&searchText=law
Instantly, the Pro search interface unlocked — returning extended results, premium datasets, and saved search tools.
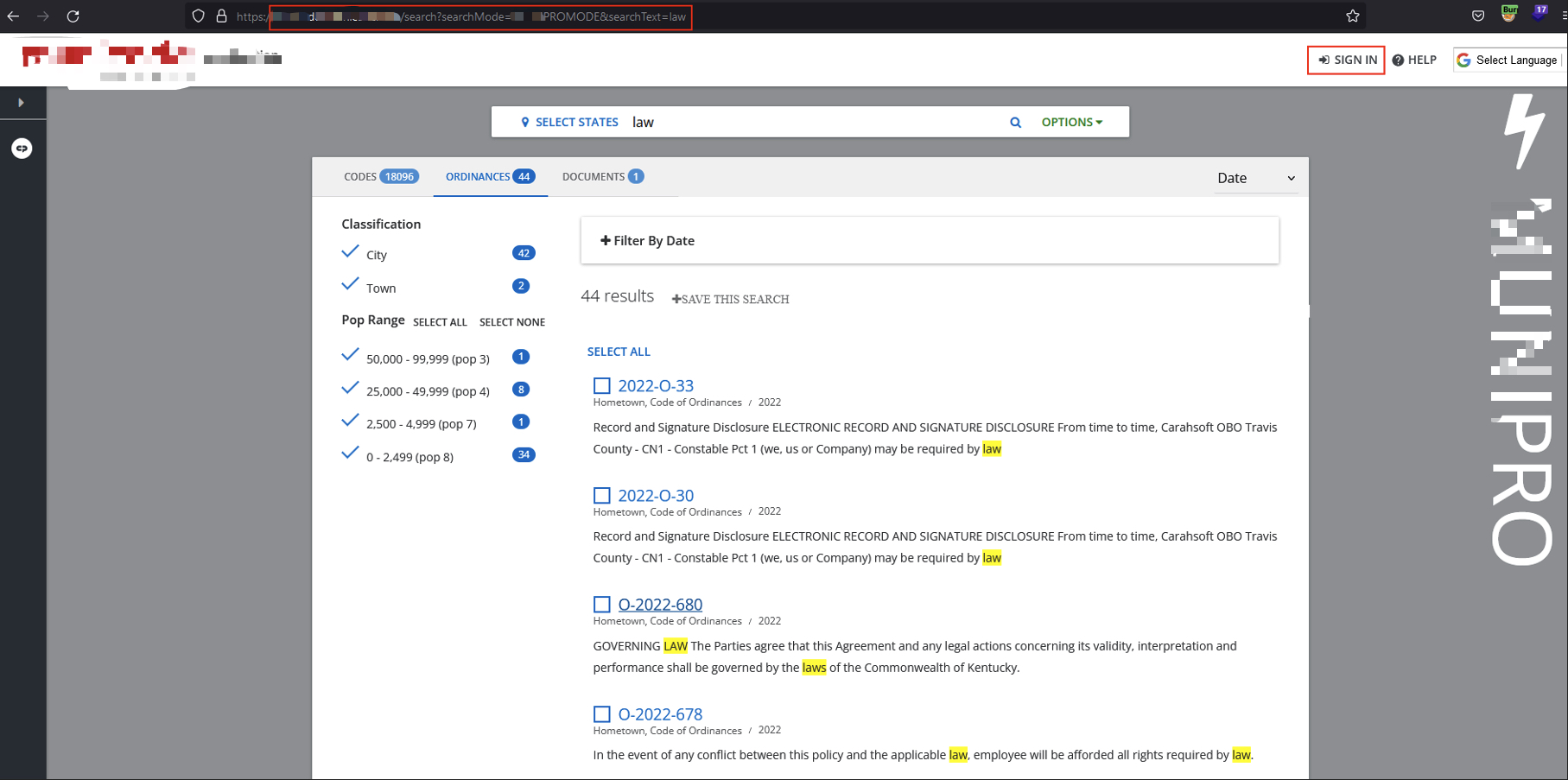
Switching the query parameter unlocked full Pro functionality.
✅ Step 3: Confirm Full Access
Verified that advanced search tools, Pro-only filters, and data visualizations were fully functional. Even account-level features like saved searches became accessible.
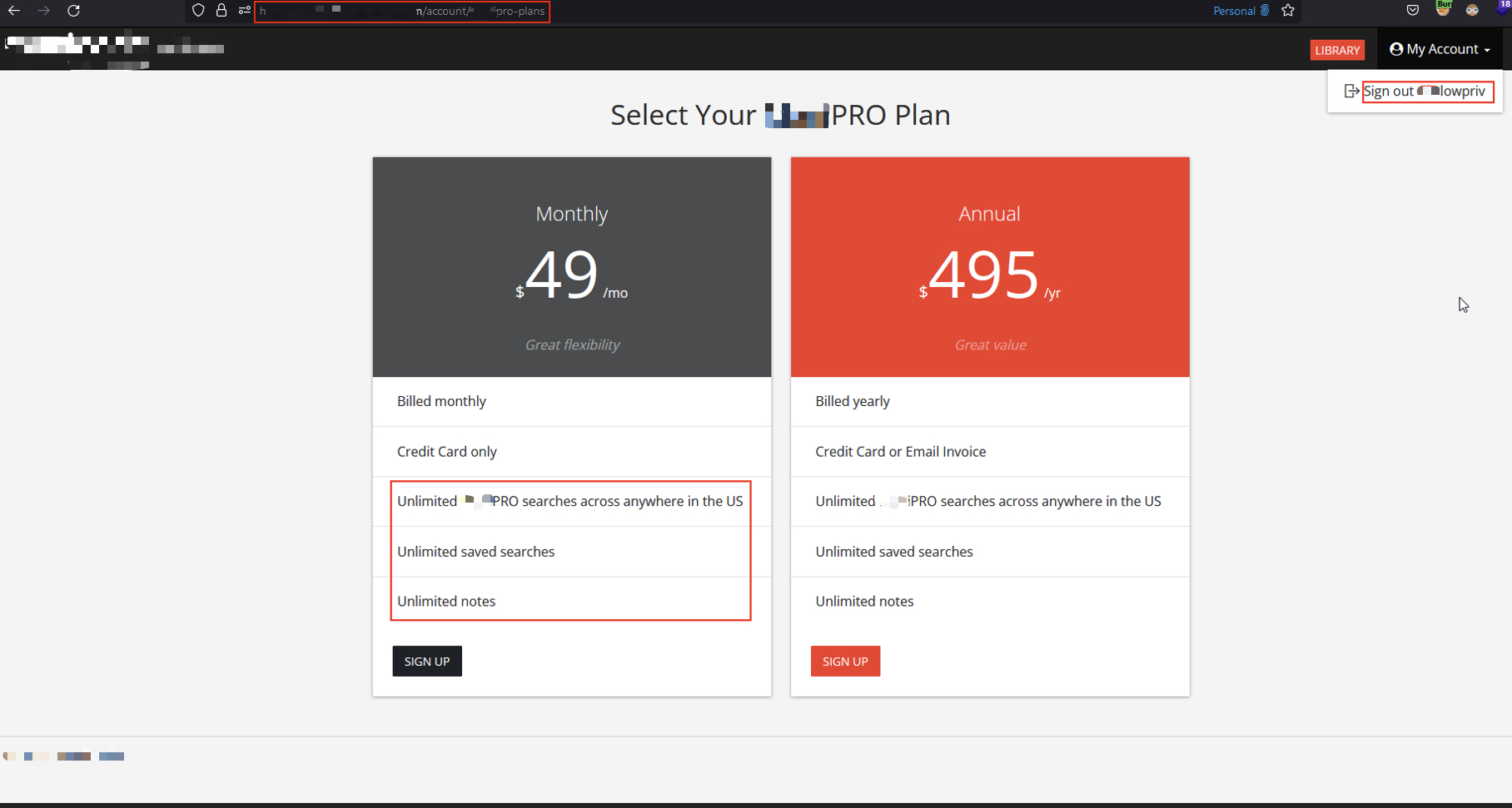
Pro-tier tools available without valid subscription.
🚪 Bonus Exploit: No Login Required
Tested the same endpoint in incognito mode (no session cookie). The backend responded identically — Pro search results returned even for anonymous users.
No authentication. No validation. Just one unguarded query flag.
🚥 Business Impact
- 💰 Direct revenue loss from premium access leakage
- 🔓 Full bypass of access control logic
- 📊 Exposure of paid subscriber features
- ⚖️ Potential legal exposure from content misuse
- ⏳ Highly scriptable and scalable for abuse
🧠 Root Cause
This wasn’t a traditional vulnerability — it was a business logic oversight:
- UI enforced restrictions visually
- Backend lacked authorization checks
- Assumed “hidden = protected”
“The door was hidden… but not locked.”
🛠️ Recommended Fixes
🔐 1. Enforce Role-Based Access
Validate user entitlements server-side before granting Pro features or results.
🚫 2. Don’t Trust the UI
Frontend visibility controls must never substitute backend permission checks.
📊 3. Monitor Feature Access
Implement telemetry to detect non-subscribed accounts using Pro features.
🔄 4. Validate Query Params
Reject or sanitize unauthorized feature parameters like searchMode=PROMODE for unentitled users.
🧠 Final Thoughts
The best vulnerabilities often don’t require breaking code — just breaking assumptions. When systems rely on frontend logic to enforce privilege, a single URL parameter can become the key to everything.
This was a reminder that access control is not a visual feature — it’s a backend responsibility.